Firewall Architectures
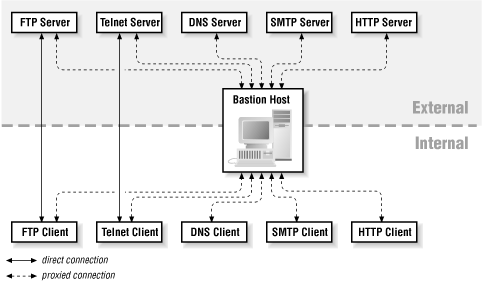
Bastion Host
def ) A bastion host is a system identified by the firewall administrator as a crtitical strong point in the network’s security.
Bastion Host는 이름처럼 어그로가 집중되는 곳으로 다른 서비스에 대한 위협을 감소시키는 목적으로 운용되는 system이다. 여기저기서 중구난방으로 정의해놓았는데, 상기한 내용이 제일 일반적인 정의다. ( Marcus J. Ranum ) 아래 내용은 ‘보통 이래야 한다’고 적어놓은 내용들이다. 꼭 아래 내용을 모두 만족해야 bastion host인 것은 아니다.
- 해당 컴퓨터에서 보통 proxy같은 single application만 hosting한다.
- 노출도가 높다.
- 방화벽이나 라우터도 방화벽 구성 모델에 따라 Bastion host로 볼 수 있다.
- 외부 -> 내부 통신은 Bastion Host를 거쳐야 한다. (그래야 의미가 있으니까) 그래서 주로 Screened Host 같은 방식은, Packet Filtering을 따로 하기 때문에 Bastion Host에서 인증 정도만 담당한다.
6.1 Single-Box Arhcitectures
- The simplest firewall architectures have a single object that acts as the firewall.
- no defense in depth
- single point of failure
- Compared to a multiple-layer system that’s integrated with your network, a single-box architecture is cheaper, easier to understand and explain to management, and easier to get from an external vendor.
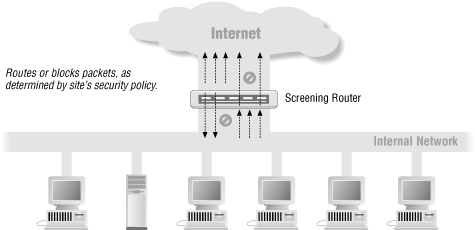
6.1.1. Screening Router
- low-cost system
- not very flexible; you can permit or deny protocols by port number, but it’s hard to allow some operations while denying others in the same protocol, or to be sure that what’s coming in on a given port is actually the protocol you wanted to allow.
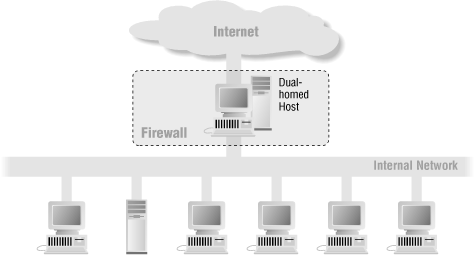
6.1.2. Dual-Homed Host
- A dual-homed host architecture is built around the dual-homed host computer , a computer that has at least two network interfaces.
- Such a host could act as a router between the networks these interfaces are attached to;
However , to use a dual-homed host as a firewall, you disable this routing function.
- routing을 disable했기 때문에, dual-homed host기준 external과 internal은 직접적으로 통신할 수 없다.
IP traffic between them is completely blocked. 대신 services를 proxying해주는 식 으로 동작한다.
어디서는 Dual-Homed Host를 2개의 Interface를 가진 Bastion host라고 표현한다. 이와 반대로 single interface bastion host는 어떤 식으로 동작할 것인지 생각해보면
이런식으로 bastion host에서 먼저 인증을 통해 토큰을 발급한 다음 내부 서비스에 접근 하는 방식으로 구성되지 않을까 싶다. packet filtering 기능 같은건 물론 기대할 수 없기 때문에 내부 네트워크에 접근 자체는 가능할 건데 서비스를 이용하는 것을 제한하는 식으로 구성할 것 같다.
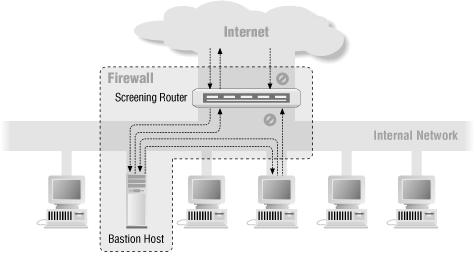
6.2.Screened Host Architectures
- Screening Router에서 packet filtering하고, Bastion Host에서 인증같은 부분을 담당하는 방식.
- The bastion host is the only system on the internal network that hosts on the Internet can open connections to.
- Any external system trying to access internal systems or services will have to connect to bastion host. The packet filtering configuration in the screening router may do one of the following: 1) Allow other internal hosts to open connections to hosts on the Internet for certain services 2) Disallow all connections from internal hosts (forcing those hosts to use proxy services via the bastion host) It is possible to mix and match these approaches for different services;
- Because the bastion host or router are a single point of failure, it is inappropriate to run high-risk services like web servers on it.
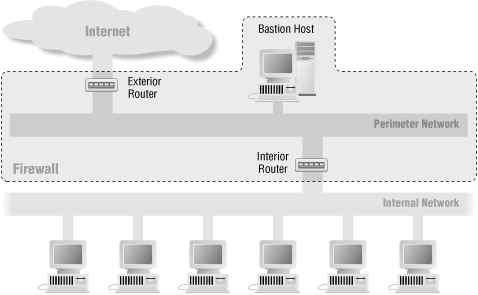
6.3.Screened Subnet Architectures
- 가장 안전함.
- 별도의 subnet을 만들어 Bastion Host를 이 곳에 위치시켜서, internal network와 분리시키는 방법.
- There is no single vulnerable point that will compromise the internal network.
- Outbound services (from internal clients to servers on the Internet) are handled in either of these ways:
- 1) Set up packet filtering on both the exterior and interior routers to allow internal clients to access external servers directly. 2) Set up proxy servers to run on the bastion host (if your firewall uses proxy software) to allow internal clients to access external servers indirectly. You would also set up packet filtering to allow the internal clients to talk to the proxy servers on the bastion host and vice versa, but to prohibit direct communications between internal clients and the outside world. In either case, packet filtering allows the bastion host to connect to, and accept connections from, hosts on the Internet;
- One of the security tasks that the exterior router can usefully perform is the blocking of any incoming packets from the Internet that have forged source addresses.
참고
http://docstore.mik.ua/orelly/networking_2ndEd/fire/index.htm